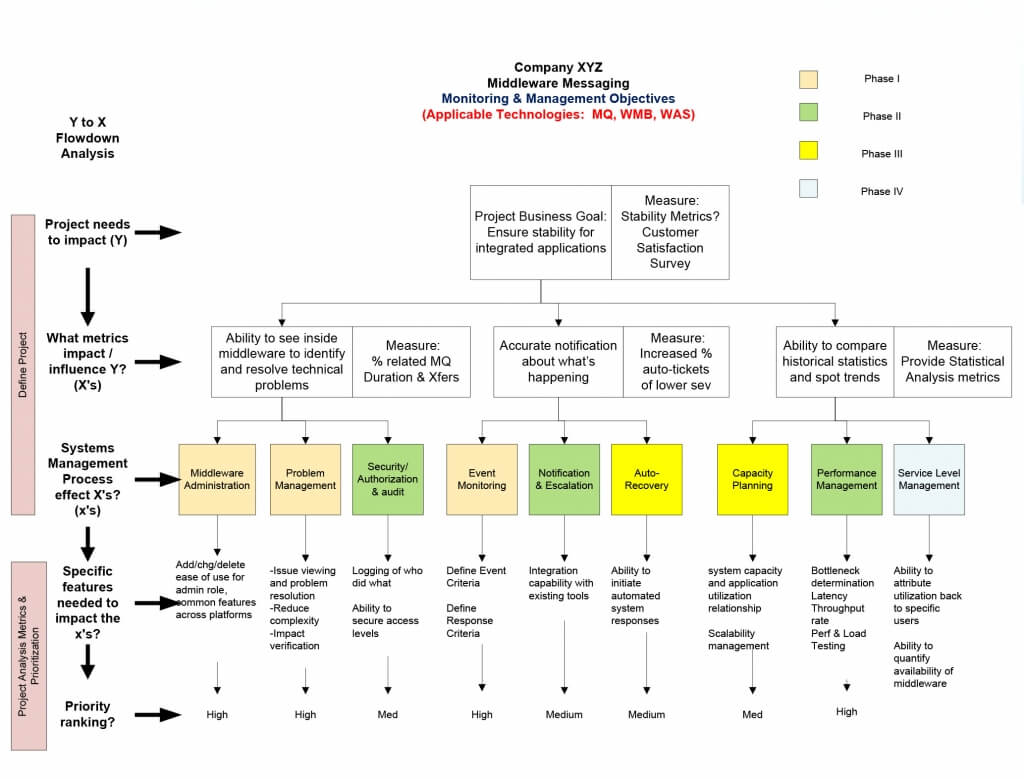
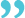Authored by Chuck Fried, President – TxMQ, Inc.
Project Description
There are countless challenges facing IT decision-makers today. Loosely, we can break them down into four categories: Cost control, revenue generation, security and compliance, and new initiatives.
There’s obvious overlap between these categories: Can’t cost control be closely related to security considerations when evaluating how much to invest in the latter? Aren’t new initiatives evaluated based on their ability to drive revenues, or alternatively to control costs? Yet these categories will at least allow us to focus and organize the discussion below.
Cost Control
Cost control has long been a leading driver in IT-spend decisions. From the early days of IT in the ’50s and ’60s, technology typically had a corporate champion who argued that failure a to invest in tomorrow would yield to customer attrition and market-share erosion. A loss of competitive advantage and other fear-mongering were common arguments used to steer leadership toward investments in something the leadership couldn’t fully grasp. Think about the recent arc on AMC TV’s Mad Men featuring an early investment in an IBM mainframe in the 1960s ad agency – championed by few, understood by even fewer.
From these early days, IT often became a black box in which leadership saw a growing line of cost, with little understanding attached to what was happening inside that box, and no map of how to control those growing expenditures.
Eventually, these costs became baked-in. Companies had to contend with the reality that IT investment was a necessary, if little-understood reality. Baseline budgets were set, and each new request from IT needed to bring with it a strong ROI model and cost justification.
In more recent years – and in a somewhat misdirected attempt to control these costs – we witnessed the new option to outsource and offshore technology. It was all an attempt to reduce baked-in IT costs by hiring cheaper labor (offshoring), or wrapping the IT costs into line-item work efforts managed by third parties (outsourcing). Both these efforts continue to meet with somewhat mixed reviews. The jury, in short, remains out.
IT costs come from five primary sources – hardware, software, support (maintenance and renewals), consulting and people. Note that a new line-item might be called “cloud,” but let’s keep that rolled into hardware costs for now. Whether cloud options change the investment equation or not isn’t the point of this paper. For now, we’ll treat them as just another way to acquire technology. There’s little, but growing evidence that cloud solutions work as a cost reducer. Instead, they more often alter the cash-flow equation.
Hardware costs are the most readily understood and encompass the servers, desktops, printers – the physical assets that run the technology.
Software, also relatively well understood, represents the systems and applications that the company has purchased (or invested in if homegrown) that run the business, and run on the hardware.
Support refers to the dollars charged by software and/or hardware companies to continue to run licensed software and systems.
Consulting means dollars invested in outside companies to assist in both the running of the systems, as well as in strategic guidance around technology.
People, of course, is the staff tasked with running and maintaining the company’s technology. And it’s the people costs that are perhaps the most sensitive. While a company might want to downsize, no one wants the publicity of massive layoffs to besmirch a brand or name. Yet a reality of a well-built, well-designed and well-managed IT infrastructure should be a reduction in the headcount required to run those systems. If a company doesn’t see this trend in place, consider it a red flag worthy of study.
How should a company control IT costs? Unless a company is starting from scratch, there’s going to be some level of fixed infrastructure in place, as well as a defined skills map of in-place personnel. A company with a heavy reliance on Microsoft systems and technology, with a well-staffed IT department of Microsoft-centric skills, should think long and hard before bringing in systems that require a lot of Oracle or open-source capabilities.
Companies must understand their current realities in order to make decisions about technology investment, as well as cost control. If a company relies on homegrown applications, it can’t readily fire all of its developers. If a company relies mostly on purchased applications, it might be able to run a leaner in-house development group.
Similarly, companies can’t operate in a vacuum, nor can IT departments. Employees must be encouraged to, and be challenged to attain certifications, attend conferences and network with peers outside of the company. Someone, somewhere already solved the problem you’re facing today. Don’t reinvent the wheel. Education is NOT an area we’d encourage companies to cut back on.
At the same time, consulting with the right partner can produce dramatic, measurable results. In the 21st century, it’s rather easy to vet consulting companies – to pre-determine capability and suitability of fit both skills-wise, as well as culturally. The right consulting partner can solve problems quicker than in-house teams, and also present an objective outsider’s view of what you’re doing right, and what, perhaps, you could do better. “We’ve always done it this way” isn’t an appropriate reason to do anything. A consulting company can ask questions oftentimes deemed too sensitive even for leadership. I’ve been brought in to several consulting situations where leadership already knew what decision would be made, but needed an outside party to make it and present the option to leadership so things would appear less politically motivated.
Similarly, consulting companies can offer opinions on best practices and best-product options when required. A software company, on the other hand, won’t recommend a competitor’s product. A consulting company that represents many software lines, or even none at all, can make a far more objective recommendation.
In point of fact: One of the primary roles for an experienced consulting company is to be the outside partner that makes the painful, outspoken recommendations leadership knows are necessary, but can’t effectively broadcast or argue for within the boardroom.
Innovation As Cost Control
There are several areas of technology spend with legitimately demonstrated ROI. Among these are BPM, SOA, process improvement (through various methodologies and approaches from six sigma to Agile development among many others), as well as some cloud offerings previously touched on.
BPM, or business-process management, broadly describes a category of software whereby a company’s processes, or even lines of business can be automated to reduce complexity, introduce uniformity and consistency of delivery, and yes, reduce the needed headcount to support the process.
We’re not talking about pure automation. Loosely, BPM refers to a system that cannot be fully automated, but can be partially automated yet still require some human interaction or involvement. Think loan application or insurance claim. Many of the steps can be automated, yet a person still has to be involved. At least for now, a person must appraise a damaged car or give final loan approval.
SOA, discussed elsewhere in this paper, means taking advantage of a loosely coupled infrastructure to allow a more nimble response to business realities, and great cost controls around application development and spend. Process improvement, of course, means becoming leaner, and better aligning business process with business realities, as well as ensuring greater consistency of delivery and less stress on internal staff due to poor process control.
Big Data As Cost Control
Big data, discussed later in this paper, can also be used, or some might say misused, to drive down costs. An insurance company can use data analysis to determine who might be too costly to be covered any longer. A bank might also feel certain neighborhoods or even cities are too risky to offer loans. There’s a dark side to big data. At times even unintended consequences may result. It’s important for human oversight to remain closely aligned to system-generated decisions in these nascent days of big data. While Google may have figured out how to automate the driving process, companies today are still hopefully more than a few years away from 100% automated decisioning. One hopes society, as much as government oversight will help ensure this remains the case for the foreseeable future.
Integration And Service Oriented Architecture As Cost Control
Too often companies rely on disparate systems with limited, if any ability to interact. How often have you been logged on to your bank’s online system, only to have to log on a second time to access other accounts at the same institution?
Companies must be quick to recognize that consumers today expect seamless, complete integration at all points of their interaction. Similarly, suppliers and trading partners are ever more expectant of smooth onboarding and ease-of-business transacting. Faxing purchase orders is yesterday. Real-time tracking and reordering of dwindling products in the supply chain is the new normal.
At the same time, companies must recognize that to be nimble and adaptable against the ever-changing reality of their businesses, applications must be designed and implemented differently. It’s one thing if a company has five different systems and no more. A simple 1980s-era point-to-point architecture might suffice. Yet other than that limited example, enterprises show an ever-changing array of systems and needs. Hardcoding applications to each other yields an inflexible and challenging infrastructure that’s cost-prohibitive to change.
Yet other than that limited example, enterprises show an ever-changing array of systems and needs. Hardcoding applications to each other yields an inflexible, and challenging infrastructure that’s cost prohibitive to change.
An Enterprise Service Bus, or ESB, is what most enterprises and midmarket companies today recognize as a model architecture. Decoupling applications and integrating them loosely and asynchronously enables rapid application design and more nimble business decision-making. At the same time, an SOA-enabled environment also allows for the rapid adoption of new products and services, as well as the rapid rollout of new offerings to customers and trading partners. Yes, this does require a changing of attitudes at the development, QA and production-support levels, but it’s a small price to pay for long-term corporate success.
Revenue Generation
The idea of IT helping companies generate new revenue streams isn’t new. It’s as old as the technology itself. Technology has always played a role in driving revenue – from airline-reservation systems, to point-of-sale systems, to automated teller machines (allowing banks to charge fees). Yet these systems didn’t create new revenues (with the possible exception of the ATM example) – they simply automated previously existing systems and processes.
Airlines were booking flights before the Internet made this possible for the mass public, and restaurants have, of course, been serving people dating back to the dawn of civilization. Technology improved these processes – it didn’t created them.
But until recently there were no app stores and certainly no online videogame communities. Not to mention the creation of entire companies whose revenue streams weren’t even theoretically possible years ago – think Netflix or Square or Uber. So new revenue streams are as likely to be the sole source of revenue for a company as they are to supplement an already in-place business model.
Perhaps one of the more exciting new-revenue developments has come to be called the API Economy. An API, or Application Programming Interface, is a bit of code or rules for how a software component should interact with other software or components. As an example, Salesforce.com has a published API to define how another application can integrate with it.
This new ecosystem is based on what grew out of web-browser cookies years ago. Cookies are bits of data on individuals’ personal systems used to identify returning visitors to websites. Today, the API economy describes how and why our browsers look the way they do, why we see which ads where, and much more. A visit today to most websites involves that site looking at your profile and comparing it to data that particular company has on you from other APIs it might own or subscribe to. Facebook, Google, Amazon and others allow companies to target-market to the visitor based on preferences, other purchases and the like. Similarly, one can opt in to some of these capabilities to allow far greater personalization of experiences. A user might opt in to a feed from Starbucks, as well as a mall he or she frequents, so upon entry to the mall, Starbucks sends a coupon if the guest doesn’t come in the store on that particular visit.
Big Data As Revenue Generator
Taking a bit of the API example from above a step further, companies can combine data from multiple sources to run even more targeted research or marketing campaigns. Simply put, Big Data today leverages incredible computing power, with the ever-increasing amount of publicly (and privately when allowed by individuals) data to drive certain outcomes, or uncover previously unknown trends and information.
There are a variety of dramatic examples recently cited in this space. Among them, a realization that by combining information on insurance claims, water usage, vacancy rates, ownership and more, some municipalities have been able to predict what properties are more likely than others to experience failure due to theft or fire. What makes this possible is technology’s nearly unimaginable ability to crunch inconceivably large data sets that no longer have to live, or even be moved, to a common system or platform.
In the past, to study data one had to build a repository or data warehouse to store the data to be studied. One had to use tools (typically ETL) and convoluted twists and orchestrations of steps to get data into one place to be studied. At the same time, one had to look at subsets of data. One couldn’t study ALL the data – it just wasn’t an option. Now it is.
In another dramatic and oft-cited example, it was discovered that by looking at the pattern of Google searches on “cold and flu remedies,” Google was better able than even the CDC to predict the pattern of influenza outbreaks. Google had access to ALL the data. The data set equaled ALL. The CDC only had reports, or a subset of the data to look at. The larger the data set, oftentimes the more unexpected the result. It’s counter-intuitive, but true.
How and where revenue models work within this space is evolving, but anyone who’s noticed more and more digital and mobile ads that are more and more appropriate to their likes (public or private) is experiencing Big Data at work, combined with the API Economy.
Mobile As A Revenue Generator
Mobile First. It’s a mantra we hear today that simply means companies must realize that their customers and employees are increasingly likely to access the company’s systems using a mobile platform first, ahead of a desktop or laptop device. It used to be an afterthought, but today a company must think first about deploying its applications to support the mobile-first reality. But how can mobile become a unique revenue driver?
Outside of apps in the Android and Apple App stores, companies struggle with use cases for mobile platforms. This author has seen the implementation of many creative use cases, and there are countless others yet to be imagined. Many retailers have followed Apple’s model of moving away from fixed checkout stations to enable more of their employees to check people out from a mobile device anywhere in the store. Similarly, many retailers have moved to tablets to enable their floor employees to remain engaged with consumers and to show the customers some catalog items perhaps not on display. The mobile platform can even be used to communicate with a backroom clerk to bring out a shoe to try on while remaining with the guest. It’s a great way to reduce the risk of an early departure. A strong search application might also allow the retailer to show the customer what other guests who looked at the item in question also looked at (think Amazon’s famous “others who bought this also bought these” feature). We’ll discuss mobile further later in this paper.
Security and Compliance
Not enough can be said about security. All vendors have introduced products and solutions with robust new enhancements in security – from perimeter hardening to intrusion detection. Yet security begins at home. Companies must begin with a complete assessment of their unique needs, capabilities, strengths and weaknesses. There’s no such thing as too much security. A bank might know it can require fingerprint verification, photo id and more at the point of sale prior to opening a new account. Yet that same bank might also acknowledge that too high a barrier might turn off the very customers it needs to attract. It’s a delicate tightrope.
All experts agree that the primary security threats are internal. More theft happens from within an organization than from without. Proper procedures and controls are critical steps all enterprises must take.
The following areas we can loosely discuss under the Security and Compliance umbrella. While they may or may not all tightly fit herein, it is the most useful group to place them in for our purposes.
Mobile Device Diversity And Management
Mobile’s everywhere. Who among us doesn’t have at least one, if not many mobile devices always within arm’s reach at all times, often at all hours of the day? It’s often the first thing we check when we rise in the morning and the last thing we touch as we lay down at night. How can companies today hope to manage the desires of their employees to bring their own devices to work and plug into internal systems? Then there’s the concern about choosing what platforms can and should be supported to allow for required customer- and trading-partner interaction, not to mention securing and managing these devices.
A thorough study of this topic would require volumes and far greater study than is intended here. Yet a comprehensive device strategy is requisite today for any midmarket to enterprise company, and a failure to recognize that fact will lead only to disaster. A laptop left in a cab or a cell phone forgotten in a restaurant can lead to a very costly data breach if the device isn’t both locked down, as well as enabled with a remote-management capability to allow immediate data erasure.
As to enabling customer and partner access: As stated earlier, companies are made up of people, and people are more likely to access a system today from a mobile device than from a desktop. It’s crucial that companies engineer for this reality. A robust mobile application isn’t enough. Customers demand a seamless and completely integrated frontend to backend system for mobile to mirror a desktop-quality experience.
Cloud
So what is a cloud, and why is everyone talking about it? As most realize now, cloud is a loose term meant to refer to any application or system NOT hosted, run or managed in the more traditional on-premises way. In the past, a mainframe ran an application accessed by dedicated terminals. This evolved to smaller (yet still large) systems also with dedicated “slaved” terminals, and later to client-server architecture where the client could run its own single-user systems (think MS Office Suite) as well as access back-end applications.
Cloud applications are easiest thought of as entire systems that are simply run elsewhere. Apple’s App Store, Salesforce.com, online banking and many examples too numerous to mention are typical. Companies today can also choose to have their traditional systems hosted and run, and/or managed in the cloud, but can also architect on-premises clouds, or even hybrid on- and off-premises clouds.
The advantages are numerous, but the pitfalls are too. Leveraging someone else’s expertise to manage systems can produce great returns. Yet companies often fail to properly negotiate quality-of-services and SLAs appropriate to their unique needs, and complain of poor response time, occasional outages and the like. We can’t even begin to address the security implications about Cloud, including what customer data, or patient data can, and cannot be stored off premises.
There are countless consulting firms that can guide companies needing help to navigate the messy landscape of cloud options and providers.
New Initiatives:
Internet Of Everything (IOT)
A web-enabled refrigerator? A thermostat that can automatically set itself? A garage door that can send an email indicating it was left open? GPS in cars, watches and phones? These are just a few of the ideas we once thought silly, or simply couldn’t conceive of yet. But they’re a reality today. Right now we’re like the 1950s science-fiction filmmaker: We’re unable to foresee the depth and degree to which this will all end up, and what we can comprehend will probably seem silly and simple a decade from now.
CIOs and IT decision-makers today are faced with a never-ending list of things to worry about and think about. Today the IOT is a complex maze of what-ifs where reality seems to grow murkier, not than clearer at times. What is clear, though, is that just because something can be done doesn’t mean it should be done. Many of these interesting innovations will lead to evolutionary deadends as surely as the world moved away from VCRs and Walkman cassette players. Tomorrow’s technology will get here, and the path will likely be as interesting as the one we’ve all followed to make it this far.
CIOs must continue to educate and re-educate themselves on technology and consumer trends. This author found himself at a technology conference recently with executives from several global technology companies. Also in attendance was the author’s 17-year-old son, who quickly found himself surrounded with IT leaders asking his opinion on everything from mobile-device preferences to purchasing decisions in malls. When the dust settled, the teenager turned to the author and said rather decisively: “They all have it mostly wrong”.
Cloud, discussed earlier, as well as new mobile offerings can also be fit under this category of discussion.
Personnel And Staffing
More has likely been written on the topic of personnel and staffing in recent years than on all the above topics combined, and thus we left it as a unique item for final thought. Companies struggle with identifying talent to fill all of their vacant positions. At the same time, the populace complains that there aren’t enough jobs. Where’s the disconnect?
The United States and most democratized nations, are at a societal inflection point. As we move beyond the industrial revolution into this new Internet or Information Age, there will be pain.
Just as the United States struggled to adjust to the move from an agrarian society to an industrial one, we now struggle yet again.
We must be careful to not make pendulum-like moves without a careful study of the consequences – both intended and otherwise. It’s very difficult to change the momentum of a pendulum, and some policy decisions are difficult to undo.
There is an income gap. No economist would argue against that point. Wealth continues to accumulate at the top and leave a growing gap between the haves and have-nots. Some of this is expected and will settle out over time, yet most requires broad-based policy decisions on the part of lawmakers and corporate leaders alike.
Education reform and immigration reform are the tips of the iceberg we must begin to tackle. Yet we must also tackle corporate resistance to a more mobile workforce. Too often this author hears of a critical technology position that remains vacant because the employer refuses to hire a remote worker who could very readily do the job, and perhaps at a lesser cost attributed to their willingness to work for less from their home.
While technology leaders like IBM, Oracle, HP, Microsoft and others have quickly moved to adopt this paradigm, corporate America has moved rather more slowly.
Wherever we arrive at in the future, it will be the result of decisions made today by leaders facing a rather unique set of challenges. Yet never before have we had access to the amount of information we have today to make those decisions.
With careful thought, and proper insight, the future looks rather exciting.

 We also wanted to make sure that the solution would support us for years to come, not just a year or two. By the time we were done, we were pretty confident with the decision that we made. Overall we feel the solution was appropriate for Medical Mutual.
We also wanted to make sure that the solution would support us for years to come, not just a year or two. By the time we were done, we were pretty confident with the decision that we made. Overall we feel the solution was appropriate for Medical Mutual.